Recently, AWS announced the availability of VPC resource map. Resource map shows all of the resources in a VPC and how they are connected. Which is great – knowing what you have and how all of it is connected is the first step in all sorts of tasks. AWS has a long history of building tools to help understand the AWS environment. But when I talk with customers, the next question is always, “hey – visibility is great, but what do I do next to accomplish my job?” More succinctly, how do I move beyond that initial step of visibility and get to the task I’m actually doing (for which visibility is step 1)?
Re-Use Is Good, Right?
Re-use is the hallmark of simplicity and architectural elegance. But AWS has a penchant for re-use for its own purposes (which is elegant), not for customers. Whether VPC resource map, Neptune, or AWS WAF, there are plenty of examples of AWS re-using components to deliver more cool little tools – but this re-use doesn’t help enterprises get their jobs done.
To get things done, organizations need to spend time and effort integrating all of the AWS widgets, plus add some of their own innovation to deliver a solution to a particular problem (e.g., to answer the question – what resources do I have, how are they connected, what security measures and controls are in place, and what am I missing?). All of this integration is fine – if that’s your business. If, on the other hand, you are not an integrator, or an organization with lots of developers with some time on their hands, this presents a challenge – and a requirement to seek a more turn-key solution. The bottom line on AWS’ widgets is that they aren’t designed to solve a customer problem – they are often just built to fill a gap in the architecture diagram or because the widget filled a need for AWS.
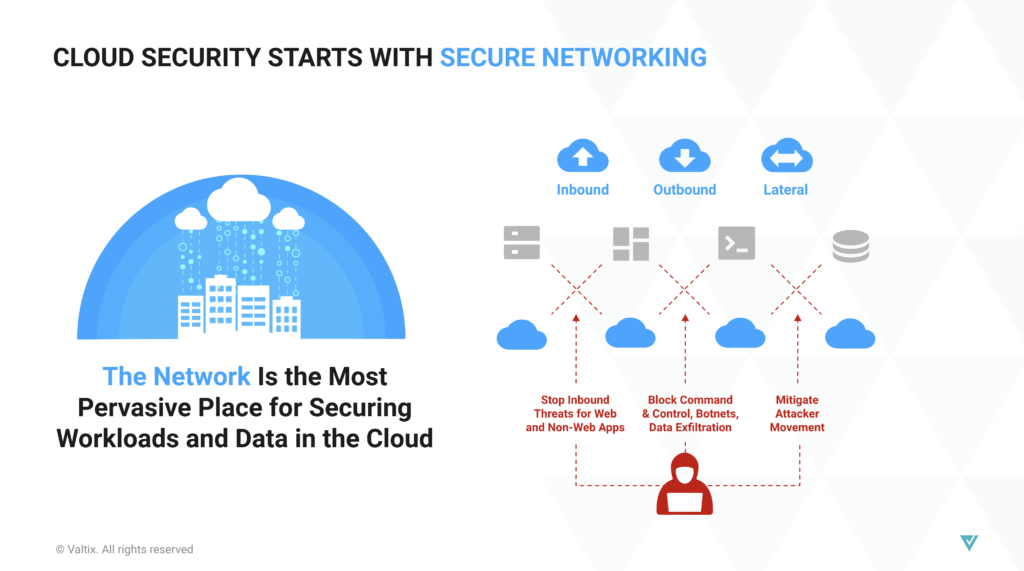
Valtix Is Focused on Secure Cloud Networking
At Valtix, we’re focused on solving a single problem – how to secure workloads in the cloud. All clouds. We do this using an approach we call secure cloud networking, focused on securing cloud workloads using a set of security services embedded into each cloud, and brought to bear with an overarching policy and control plane. All of this operates under a particular premise – given the dynamic nature of connectivity in the cloud, any approach to security that doesn’t have some degree of visibility and control over connectivity is going to have significant gaps that grow over time.
Obviously, visibility (understanding what exists across clouds, how those resources are connected, how those resources are talking, who they are talking to, and what security controls are in place to mitigate risks) is a critical piece of the Valtix solution. But all of that visibility exists to serve one purpose – to secure an organization’s workloads across any cloud they may be deployed in. Focus, in many cases, is what one DOESN’T do– so Valtix isn’t especially concerned with other uses of visibility – just everything that pertains to security.
A quick note on the multi-cloud angle – nearly every enterprise is multi-cloud, whether they like it or not. We all know that siloed visibility and security are ineffective. So any solution that is single cloud might help that cloud, but not the multi-cloud enterprise.
This brings us to the second part – now that we have the right visibility (multi-cloud, in service of security), what do we do about it? That’s the next blog – creating policy that protects workloads across every cloud.