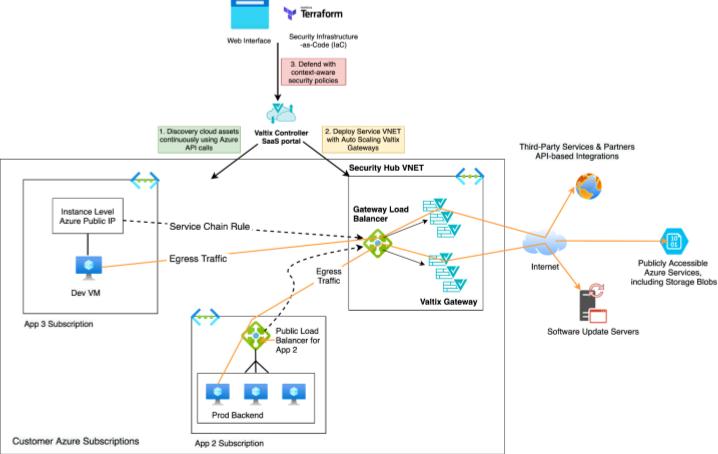
Azure Gateway Load Balancer provides a way for customers to use service chaining concepts from the software-defined networking (SDN) world to deploy advanced network security as a service to protect their applications. This simplifies putting network virtual appliances (NVAs) like Valtix Gateway in the traffic path with no changes to the customer’s virtual network (VNet) in Azure.
What’s New About Azure Gateway Load Balancer
Valtix is now offering preview support for the Azure Gateway Load Balancer, which at launch is supported for protecting egress traffic, i.e. outbound traffic to the Internet. Customers should follow Azure documentation and enrollment process for Gateway Load Balancer and can then request access to the preview support from Valtix.
Previously, Azure customers were able to add Valtix Gateways in the traffic path, however, they were not able to do so transparently and required manual route configuration using user-defined route (UDR) tables. Azure Gateway Load Balancer now makes placing Valtix Gateways in the traffic path without the need for any manual route changes. The service chaining capabilities of Gateway Load Balancer ensures that any egress traffic from VMs with public IPs can be automatically routed to Valtix Gateways for inspection even without an explicit UDR.
How Valtix Improves Security in Azure
Valtix is incorporating this preview launch into our existing hub-and-spoke architecture where Valtix Gateways run in the Service VNet hub to protect multiple spoke VNets with applications. The Service VNet and Valtix Gateways are deployed with a few clicks from the Valtix Controller web portal or via Terraform. This means that even if application and DevOps teams have local control of their VNet, security administrators can ensure that traffic is inspected by the advanced network security of Valtix before leaving the Azure VNet. This prevents exfiltration and connections to malicious sites even on VMs with public IPs.
And, of course, Valtix simplifies this entirely with point-and-click ease of use from the Valtix Controller web portal or via the Terraform provider for Valtix. More importantly, instead of managing individual NVAs for traditional NGFW and Cloud WAF appliances, Valtix Controller manages the entire lifecycle of Valtix Gateways as a service. This includes deployment, configuration, auto-scaling, software updates with blue/green style updates without any downtime, and threat intelligence updates.
This improves the operational efficiency of security administrators who can reduce the work of creating and managing network security infrastructure, and focus on actual security work.
Valtix is the first and only multi-cloud network security platform delivered as a service that enables cloud teams to meet the most stringent security requirements in a cloud-first & simple way. Valtix Controller is a service that:
- Provides continuous visibility of your Azure cloud assets at scale across multiple resource groups, VNets, and Azure subscriptions.
- Shows which VNets and instances (VMs) may be connecting to malicious IPs using NSG flow logs. This helps customers determine which workloads are under attack and maybe exfiltrating data with connections to command-n-control (C2).
- Provides automated deployment of Valtix Gateways which provides robust network security to inspect encrypted and unencrypted traffic, including: WAF, IDS/IPS, antivirus and antimalware, FQDN, and URL filtering, DLP.
- Customers can use the existing, fully supported, deployment of Valtix Gateways for securing ingress, egress, and east-west traffic, or they can try the preview mode for Azure Gateway Load Balancer to secure egress traffic. Future support for securing ingress and east-west traffic is planned.
- Creation of dynamic, context-aware, security policies using the continuous cloud asset discovery.
Using the continuous cloud asset discovery, Valtix customers on Azure can define context-aware egress security policies. For example:
| Valtix Policy | Source | Destination + Service | Rule | Valtix Inspection Rules |
| Egress-PCI- Prod- Updates |
“PCI” “Prod” “Linux” |
github.com/myOrgRepo *.redhat.comProd-Storage-Azure-Blob |
Allow + Log | Forward Proxy with TLS decryption, URL filtering, DLP (no credit cards, SSNs), IDS/IPS, AV |
| Egress-Dev- | “Dev” | *.github.com Dev-Storage-Azure-Blobs *.canonical.com |
Allow + Log | Forward Proxy with TLS decryption, URL filtering, IDS/IPS, AV |
| Approved-Azure-PaaS | “Prod” “Dev” |
Org-AzureStorage-Blobs Azure KeyVault Azure SQL CosmosDB |
Allow + Log | Forward Proxy with TLS decryption, FQDN filtering |
| Unapproved-Azure-PaaS | “Prod” “Dev” |
Azure-OMS Azure-HDInsight |
Forwarding, FQDN filtering | |
| East-West Segmentation for Prod | “prod” “web-tier” |
“prod” “App-tier1” |
Allow + Log | Forward Proxy with TLS decryption,
IDS/IPS, Antivirus, DLP (max 1 SSN per session) |
| Block Malware Bots and C2 | Any | Malicious FQDN category, Malicious IP list | Deny + Log | Forwarding, FQDN filtering |
To Learn More:
- To test the preview availability of Azure Gateway Load Balancer or to learn more contact us.
- Valtix Documentation for Azure
- Azure Blog on Gateway Load Balancer
Azure documentation on Gateway Load Balancer.