Summary: Spring4Shell
Zero-day POC leaked online, confirmed to be a critical vulnerability in Java Spring Framework. Dubbed Spring4Shell, as a parody of Log4Shell, CVE-2022-22965 does not resemble Log4j in its breadth of impact on the underlying Internet infrastructure.
Spring Framework is a Java application model that allows for organizations to focus on their business logic needs without having to build the “plumbing”. A patch is available for affected versions, with more details available on Spring’s website.
Valtix customers with auto-updating IDS/IPS signature or virtual patching enabled, are protected from CVE-2022-22965 and CVE-2022-22963 exploitation automatically.
Overview
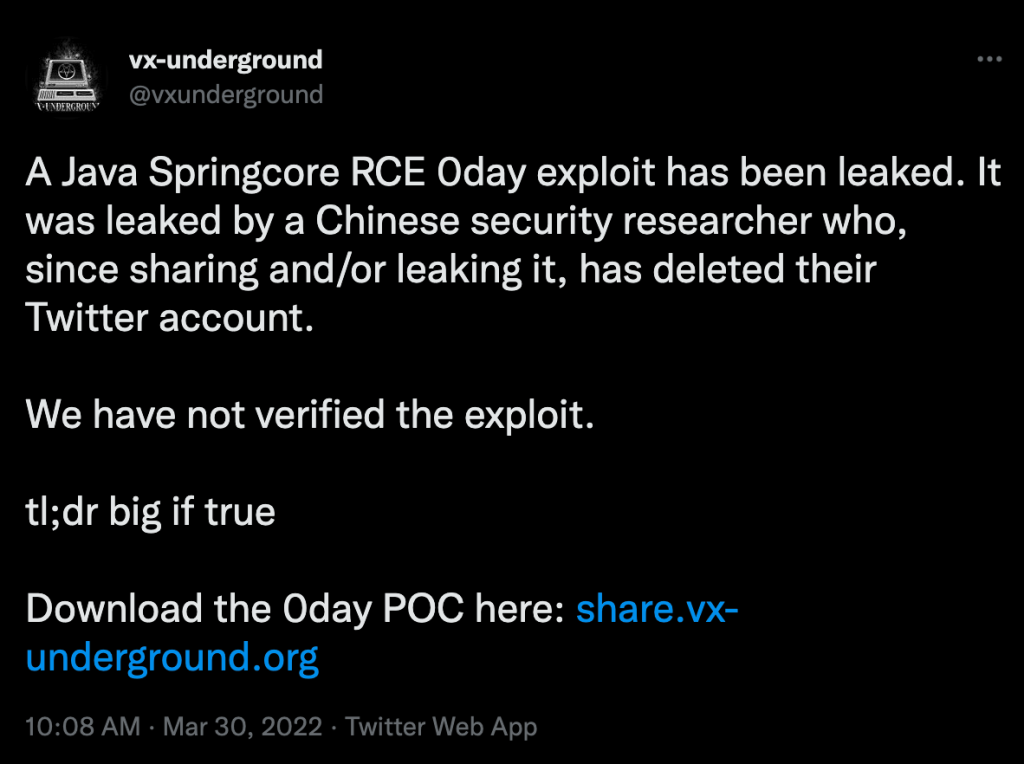
March 29th, 2022– A presumably Chinese Twitter/GitHub user, with the handle “p1n93r”, briefly released a proof-of-concept (POC) code for a Spring Framework remote code execution (RCE) vulnerability.
P1n93r quickly deleted their related social media accounts, but not before VX-Underground was able to archive the POC and provide it for public download.
As security researchers analyzed the POC, there was some initial confusion surrounding whether or not it was related to CVE-2022-22963– a critical RCE vulnerability in Spring Cloud Function affecting versions 3.1.6 and 3.2.2 that was released the same day. Spring Cloud Function is a part of Spring Cloud created to help design business logic as programmable functions.
Affected Versions & Mitigation
| CVE | Affected Versions | Mitigation |
| CVE-2022-22965 (Spring4Shell) |
|
Upgrade Spring Framework version to 5.3.18+ or 5.2.20+ |
| CVE-2022-22963 | Spring Cloud Function version 3.1.6, 3.2.2, or older | Upgrade Spring Cloud Function to version 3.1.7 or 3.2.3. |
Exploitation & Detection
Review of the POC code shows that exploitation is straightforward using Python’s requests, argparse and urllib libraries. A malicious URL can be constructed to deliver a .jsp webshell via a POST request, and upon a successful “200” status code, discovery commands like “WHOAMI” can be run to provider threat actors with details about the compromised system. Because the vulnerability relies on Class Loaders specific to Tomcat, Spring notes that other attacks are possible using a different custom ClassLoader.
Indicators of attack (IOAs) that may help network defenders triaging potentially compromised environments may include:
- URLs containing keywords/strings like: “class”, “class.module”, “classLoader”, or “class.module.classLoader.resources”
- POST requests resulting in a 200 status code
- New files with the extension “.jsp”
- System commands used for discovery
- Outbound network communications to new IP addresses or domains
- Outbound network communications on non-standard or new ports
Mitigate Spring4Shell with Valtix
Patching is always the right answer for mitigating an emerging threat – but zero days show that no application is immune to exploitation and patching takes time. Protection outside of the application creates the defense in-depth needed to stop the threats from getting in and your data leaking out. Valtix is a multi-cloud network security platform designed to help you start creating your defensive, cloud security strategy today across AWS, Azure, GCP, and OCI.
Valtix provides proactive defense for cloud workloads via cloud firewall, IDS/IPS, WAF, egress filtering, rate-limiting, threat intelligence, and virtual patching.
To learn more about virtual patching and Valtix, review our guide on how we mitigated the recent Log4J vulnerability and sign up for Free Tier.