For enterprises, security-related visibility in the cloud is critical. For many, especially as they try to gain an understanding of what they have in the cloud, how it’s set up, and what’s happening, often across multiple clouds.
Given the distributed nature and rapid pace of initial cloud efforts – organizations know they are flying more blindly than they’re used to. But there are different kinds of cloud visibility – what exists vs. what is happening, and organizations are ready for those different kinds of visibility at different points of their cloud journey.
In fact, there are often different groups involved in these different types of visibility, which, of course, require different tools and disciplines to achieve that visibility. This blog will cover the different needs for visibility and how organizations pursue those different types of visibility.
In this article, we’ll discuss what kinds of technology are best suited to achieve cloud visibility. Let’s dig in!
Content Articles:
- Two kinds of Cloud Visibility
- What does the environment look like
- What’s happening in the Cloud Environment
- So What Kind of Cloud Visibility Do Enterprises Need?
- Bottom Line: You Will Secure What You Can See
Visibility for cloud security purposes is a hot topic – the mantra, “you can’t secure what you can’t see,” is at least as true as the statement that it was adapted from (“you can’t manage what you don’t measure”). While attention is clearly focused on cloud security visibility, various vendors playing to their strengths has created significant differences in what visibility actually means.
Two Kinds of Visibility – What Is vs. What’s Happening
In talking with customers, we see two different types of security-related cloud visibility being discussed – what does the environment look like vs. what’s happening in that environment? An example from the microcosm of the security world could be: vulnerability (what COULD happen) vs. exploit (what IS happening). Let’s explore those two types a bit.
What Does The Environment Look Like (Landscape)
Visibility of the landscape deals with the scope and scale of the cloud environment, and the security configuration and compliance of the components in that environment. And, of course, the derivative analysis that builds on those understandings. Another way to say it might be – given the scope, scale, and configuration, how much risk am I carrying? Some examples:
- Do cloud workloads have malware installed?
- Do they have configuration-based indicators of compromise?
- Is there lateral movement risk?
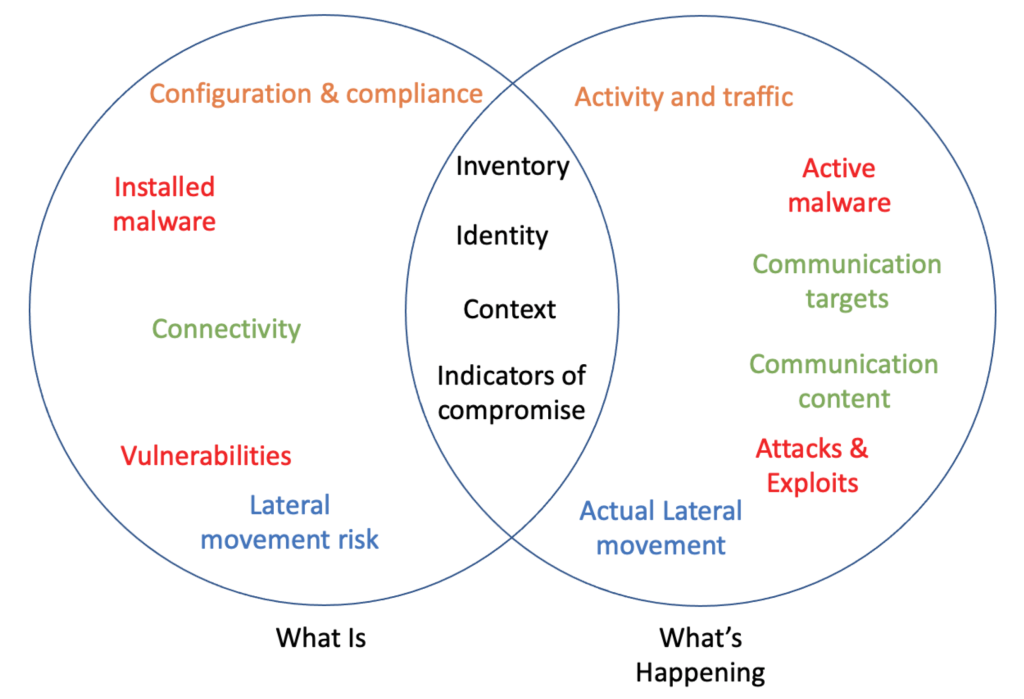
Figure 1 shows more examples and the overlap between what is vs. what’s happening, but the core information source here is the configuration – of specific workloads and the infrastructure connecting them. Nearly everything is derived from that. Back to our example, this tells you about vulnerability – what COULD happen.
What’s happening in the Cloud Environment (Activity)
Visibility of the activity within the cloud environment deals with traffic and trouble, security events, and actual threats and exploits. And the derivative analysis that information enables. Another way to say it might be: what’s happening in my environment, and what should I pay attention to, investigate, and respond to? Some examples:
- Do cloud workloads have active malware?
- Do they have traffic-based indicators of compromise?
- Is there actual lateral movement?
Again, Figure 1 shows more examples and the overlap between what is vs. what’s happening. There are workload inventory and connectivity areas of overlap, but the core information source here is traffic (and events). Nearly everything is derived from those sources. Back to our security microcosm example, this tells you about exploits – what IS happening.
In the data center world, where these types of visibility are not as easily confused, an apt comparison might be a Nessus-type scanner vs an NGFW. Where landscape-type visibility is Nessus (datacenter) or CSPM (cloud), vs. NGFW (datacenter) or Valtix (cloud).
Figure 1: What Is vs. What’s Happening
So What Kind of Cloud Visibility Do Enterprises Need?
Most organizations will need both types of visibility in the cloud. Historically, they’ve had it, and realistically, they need it. For many folks we talk with, if they don’t know what they have in the cloud, and they are just trying to come to grips with what they are doing, landscape-oriented visibility is warranted. For these organizations, many adopted cloud in a distributed fashion, and they are now trying to take on a more coherent or centralized approach.
It makes sense that their first step is getting arms around the problem, so landscape tools like CSPM are critical. Many of these tools have moved towards a continuous assessment, which is great, but it doesn’t change the nature of landscape tools – they still focus on what’s there and how it’s configured.
But, shoring up vulnerabilities in the environment doesn’t absolve one of the need to protect it. Understanding what’s happening in the environment is just as important as knowing what the environment looks like. Organically, as organizations get to a more coherent approach to the cloud, and they understand their cloud environment scope and scale, their next move is to understand what’s happening on an ongoing basis. But attackers don’t wait until your vulnerabilities are fixed, and your monitoring system is in place before they start running exploits.
Combating actual threats requires a different kind of visibility, again, focused on what apps are doing in the environment (the environment that is now better understood). Note that this visibility has to be in the app’s context – one cannot assume network-based identifiers work in the cloud, and even if they did, they wouldn’t tell you the meaning or importance of that app.
The other thing to keep an eye on is the next step. Once you understand the landscape and what’s happening on that landscape – the next step is doing something about it. That is, instituting some controls. As we see organizations going down this path, the smart folks tend to have this next step in mind as they solve for visibility. In other words, choose security-related visibility knowing how you’ll institute controls – and how that visibility will aid/augment those controls.
Bottom Line: You Will Secure What You Can See
For many organizations I speak with, I go back to the security mantra – “you can’t secure what you can’t see,” and relate it to these different types of visibility. If you can’t see vulnerabilities, you can’t secure them. But if you can’t see attacks, you can’t secure against them. Bottom line is that most organizations need both. But what’s most important at any given time depends on the organization and whether compliance with risk and regulatory standards is the priority at that time or security is. Thanks for reading!
Don’t feel like you have visibility in the cloud? Sign up for our Free Tier to try Valtix for visibility and run a Cloud Risk Assessment to uncover your gaps.