As CTO of Valtix, I’m having daily conversations with customers that continue to sharpen our vision for multi-cloud security. We’re also gaining an even stronger sense of what the enterprise requires to manage an increasingly complex picture of security across apps deployed in public cloud.
At Valtix we believe the network is the essential place to secure workloads because security can be deployed in less obtrusive yet effective ways across all app architectures. Our focus is on how you deploy security controls in cloud-native ways that can effectively stop attacks. Access to these updates is easy for Valtix customers – as common with SaaS, Valtix Controller (aka the portal), updates are transparent while Valtix Gateways residing in customer accounts are hitless with a blue-green that takes minutes.
In our Summer release, which is actually a roll-up of many releases, I wanted to highlight 3 core themes of capabilities delivered and recently announced:
- Packet streaming for cloud-native incident response
- Application dependency mapping to enable visibility and security policy creation
- Secure remote access to facilitate remote user connectivity to public cloud apps
In this blog, I’ll give you a quick rundown of the why, what, and how of each major capability.
Packet Streaming for Cloud-Native Incident Response
We’ve clearly heard from customers that due to the distributed nature of cloud and applications deployed there, network teams are often blind. They simply don’t have the visibility they were accustomed to in the data center, which is significant when it comes to the mission-critical applications they are migrating.
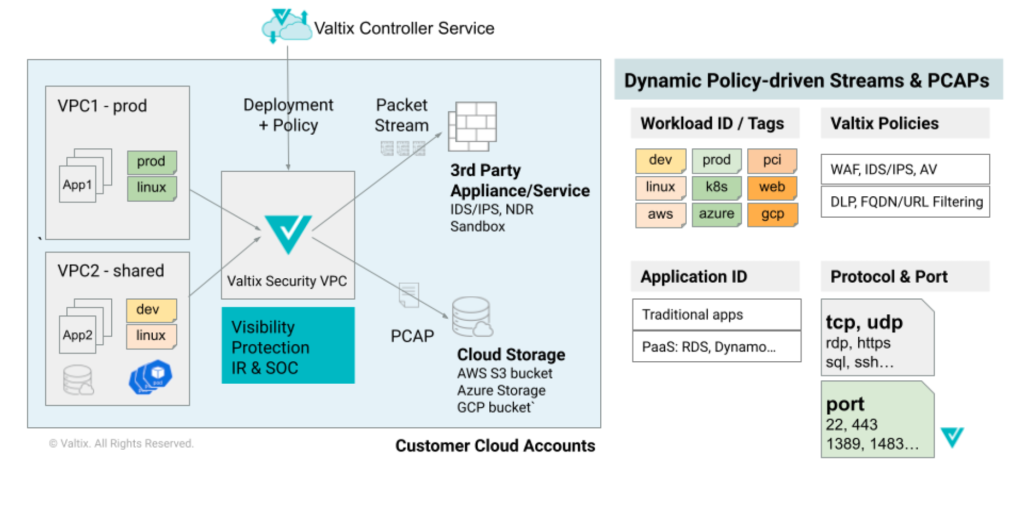
With the introduction of high-performance packet streaming capability for decrypted traffic flows, Valtix now provides an industry-leading capability as part of our platform. This augments the existing Valtix capability of packet capture (PCAP) of decrypted traffic to cloud storage buckets within the customer cloud account boundaries.
This helps organizations provide a few vital capabilities:
- Additional inspection by different network detection and response (NDR) tools and inspection by advanced non-real-time engines, such as behavioral analytics or machine learning models that require longer inference times.
- Archival of packet streams for compliance requirements and subsequent analysis by incident response (IR) and security operations centers (SOC).
Accomplishing this in public clouds is a significant challenge because:
- Cloud service providers provide packet mirroring only of encrypted packets, and there is no simple way to inspect these packets encrypted with TLS 1.2 or higher
- No cloud-native option for decrypting traffic at-scale is available from traditional decryption vendors; most rely on data center appliances ported to cloud
Key Features of Valtix Packet Streaming for Incident Response
- TLS decryption streams for forward proxy and reverse proxy to inspect ingress, egress, and east-west flows
- High performance and low latency with scalability of 100s of Gbps across a variety of commonly used cipher suites
- Multi-cloud support across AWS, Azure, GCP, and OCI
- Packet streaming for all traffic flows: ingress, egress, and east-west
- Granular packet streaming policies based on cloud account, VPC, IP/subnet or workload identity (based on tags such as dev/test/prod or web/frontend/backend)
- Meets compliance requirements to ensure that decryption keys and decrypted traffic never leaves customer cloud account boundaries
Enable Security Policy Through Application Dependency Mapping
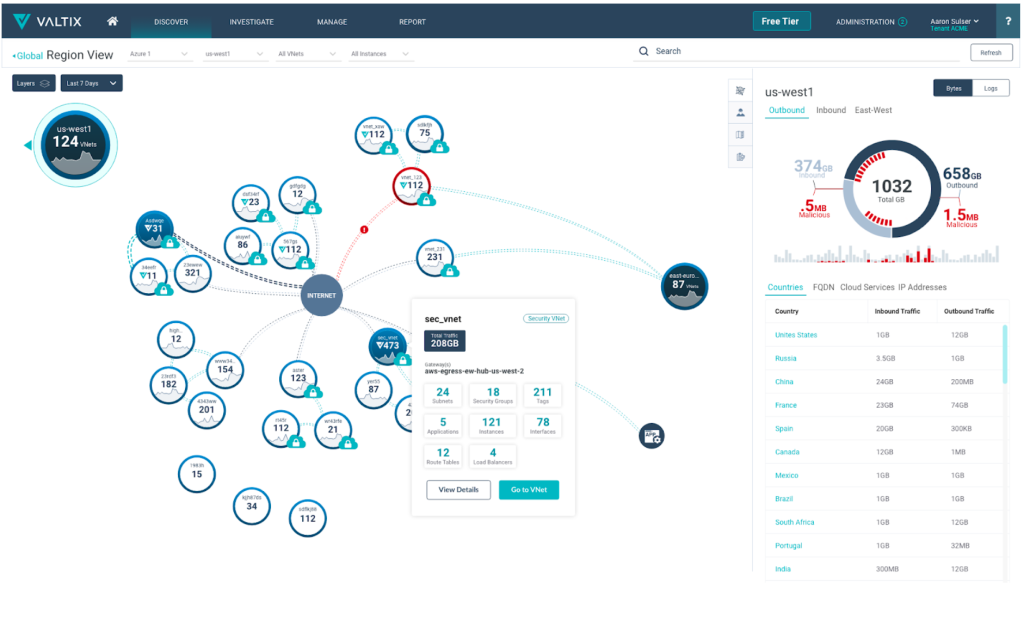
For this feature, Valtix creates application dependency maps of workloads and their traffic patterns. This data is real-time with key contextual insights.
Our philosophy has always been that the first step to protect cloud workloads is to get deep visibility in your cloud environment. As part of customer onboarding process, enterprises link their cross-cloud account roles in the Valtix Controller and Valtix Controller starts collecting cloud metadata and flow telemetry from an enterprise’s public cloud accounts. The Valtix Controller triangulates all this raw data and overlays that with threat data to produce a real-time Cloud Visibility Report, and show IOCs in customer cloud accounts.
This solution is agentless and helps enterprises define advanced network security policies. For example, allow admins to create basic network access policies between workloads within a trust boundary and create advanced network security policy (e.g. IPS or DLP) between workloads that cross a trust boundary.
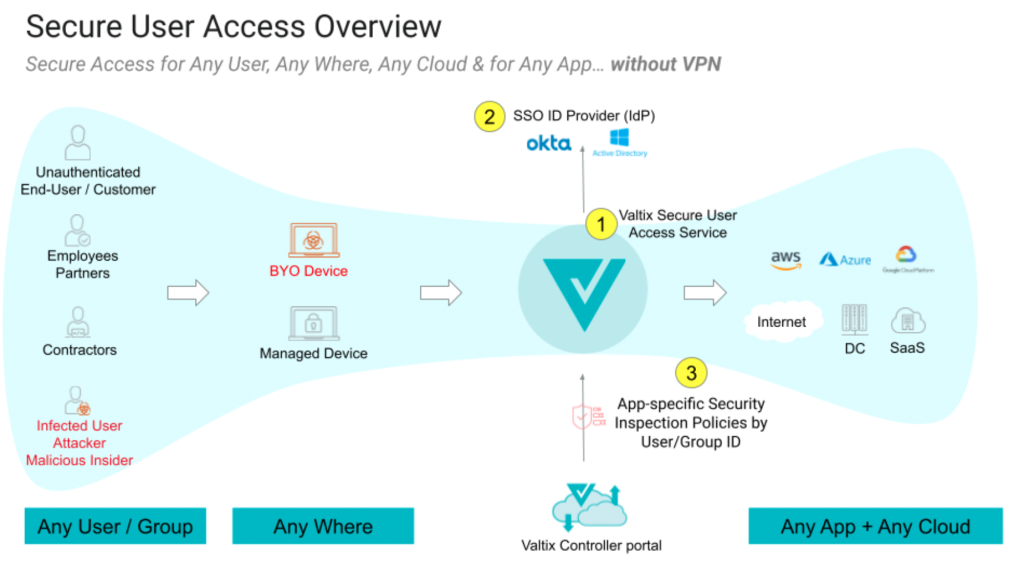
Facilitate Secure Remote User Access to Apps Running in Public Cloud
One way to understand Valtix Secure User Access is to call it an identity-aware proxy (IAP) that uses identity not just to permit access to applications, but also to apply identity-based deep packet inspection (DPI) of traffic. Ingress rules can now consume user identity to further extend zero trust for apps.
This will address two major use cases: (a) Adding advanced traffic inspection policies for Internet-facing applications based on users, groups, and application and workload identity, (b) Securing outbound/egress traffic from cloud-hosted virtual desktops (e.g. AWS Workspaces, Azure Virtual Desktop) with advanced traffic inspection policies based on user and group profiles.
Here’s how Valix is making this better:
- Continue to leverage existing SAML-based identity providers to decide who gets access to what
- Trust no one, apply user and group-based identity policies correlated with the application they are accessing, i.e. internal developers accessing dev systems are protected with policy X, contractors or consultants can only access app B and are protected with policy Y, and 3rd party/partner service connecting to service C are secured via policy Z that meets required DLP and compliance standards
- And all this with no extra work other than enabling the SSO integration in your existing Valtix Gateways and defining user/group-specific security policies
Of course, there’s so much more that I can’t cover here. If you’d like a further discussion of cloud network security and how Valtix enables security visibility and protection of cloud workloads, request a demo.